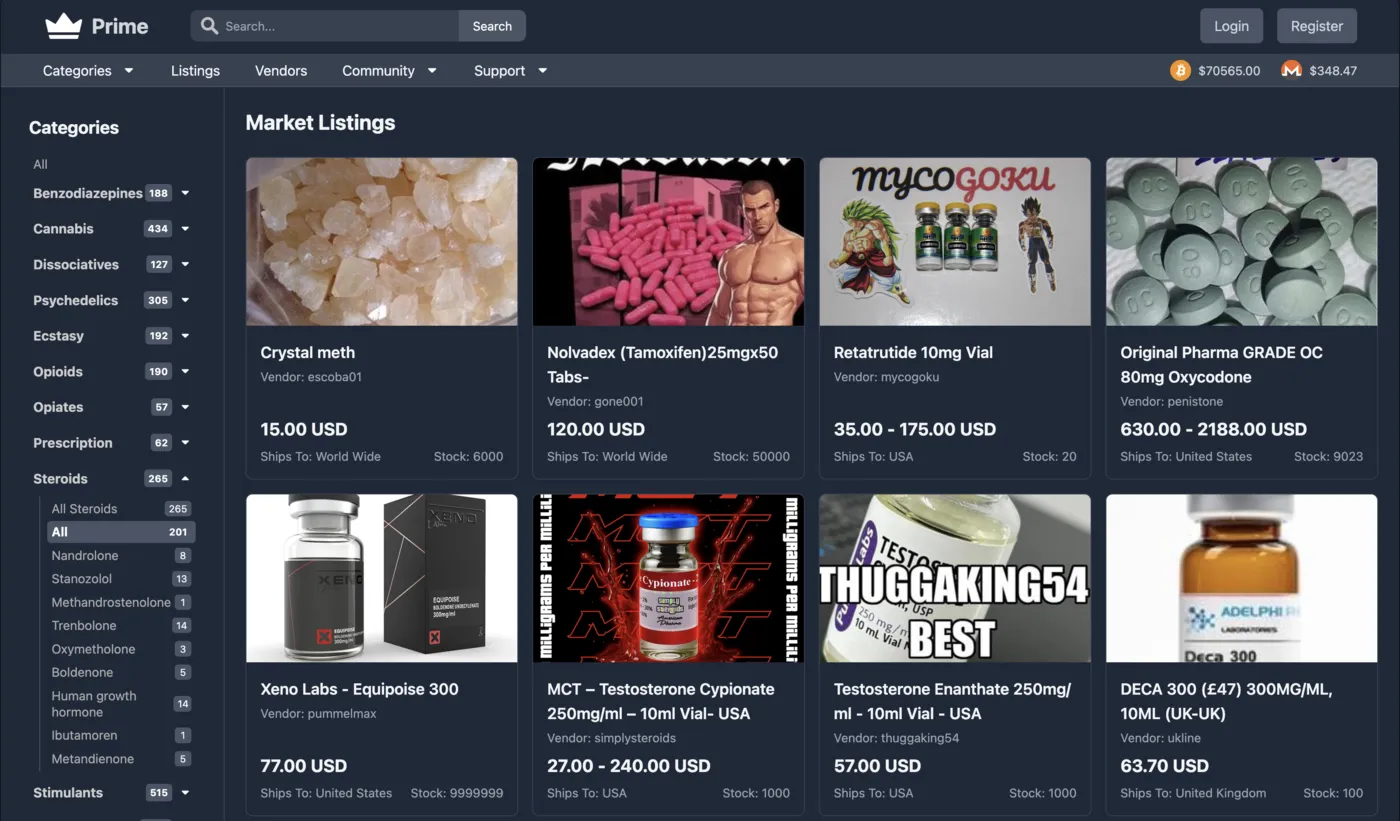
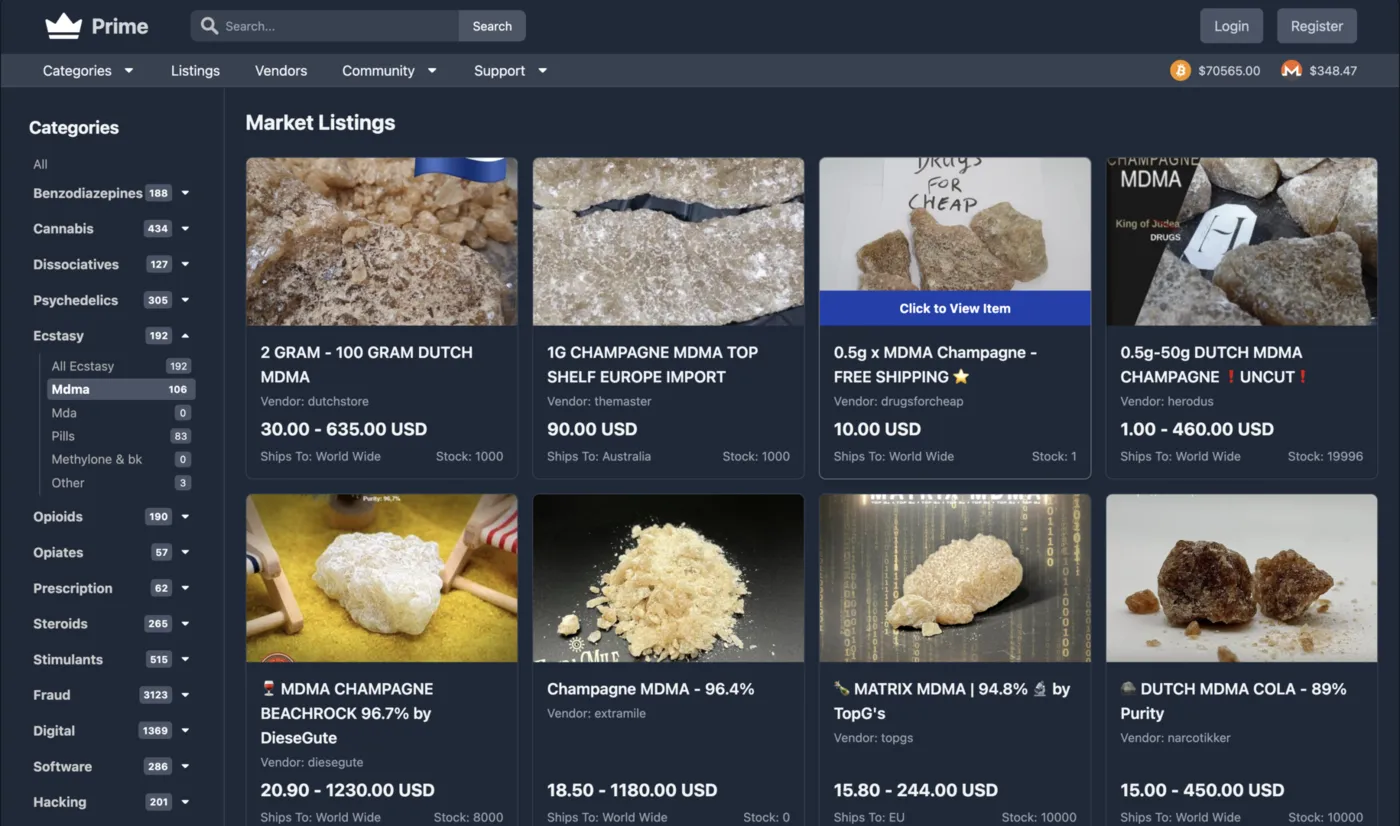
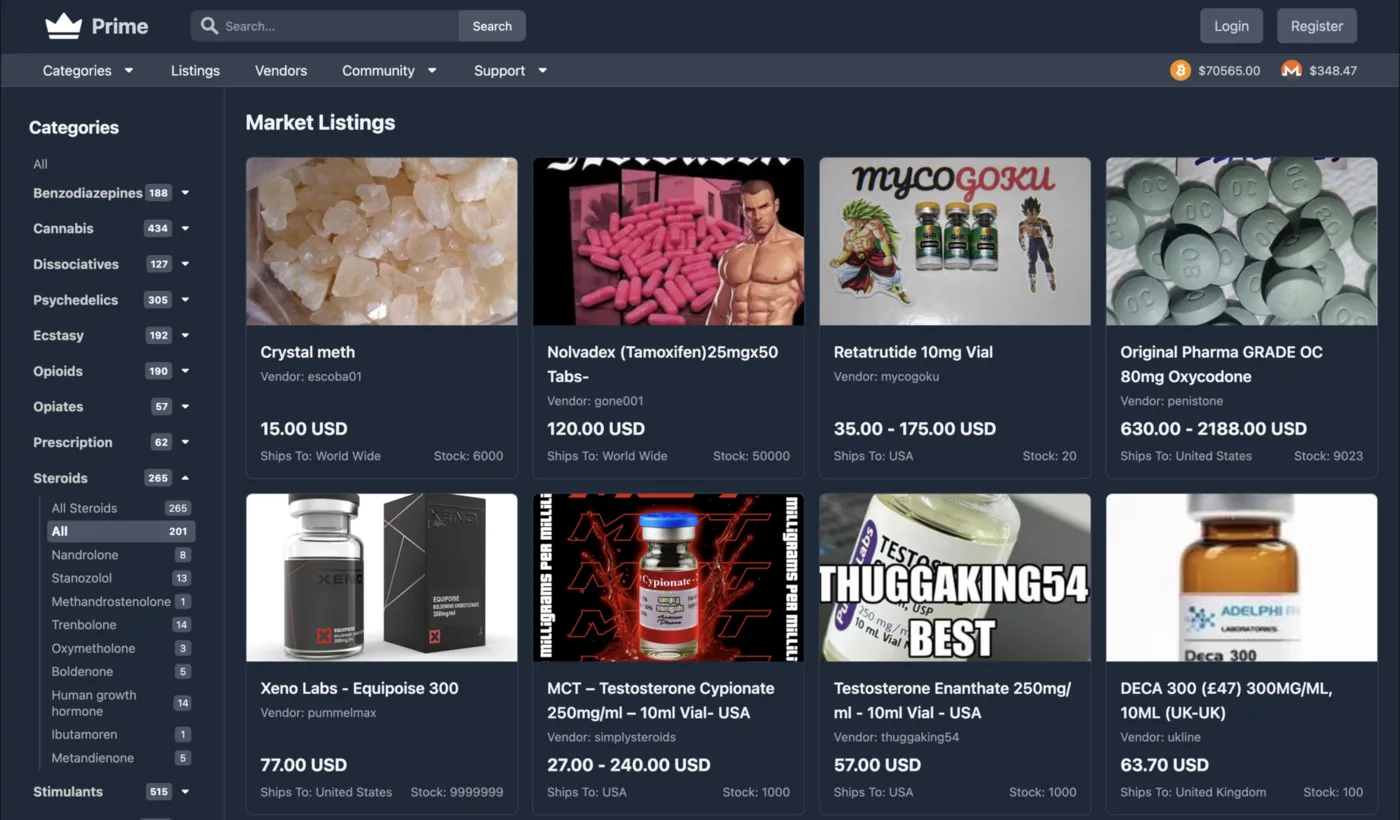
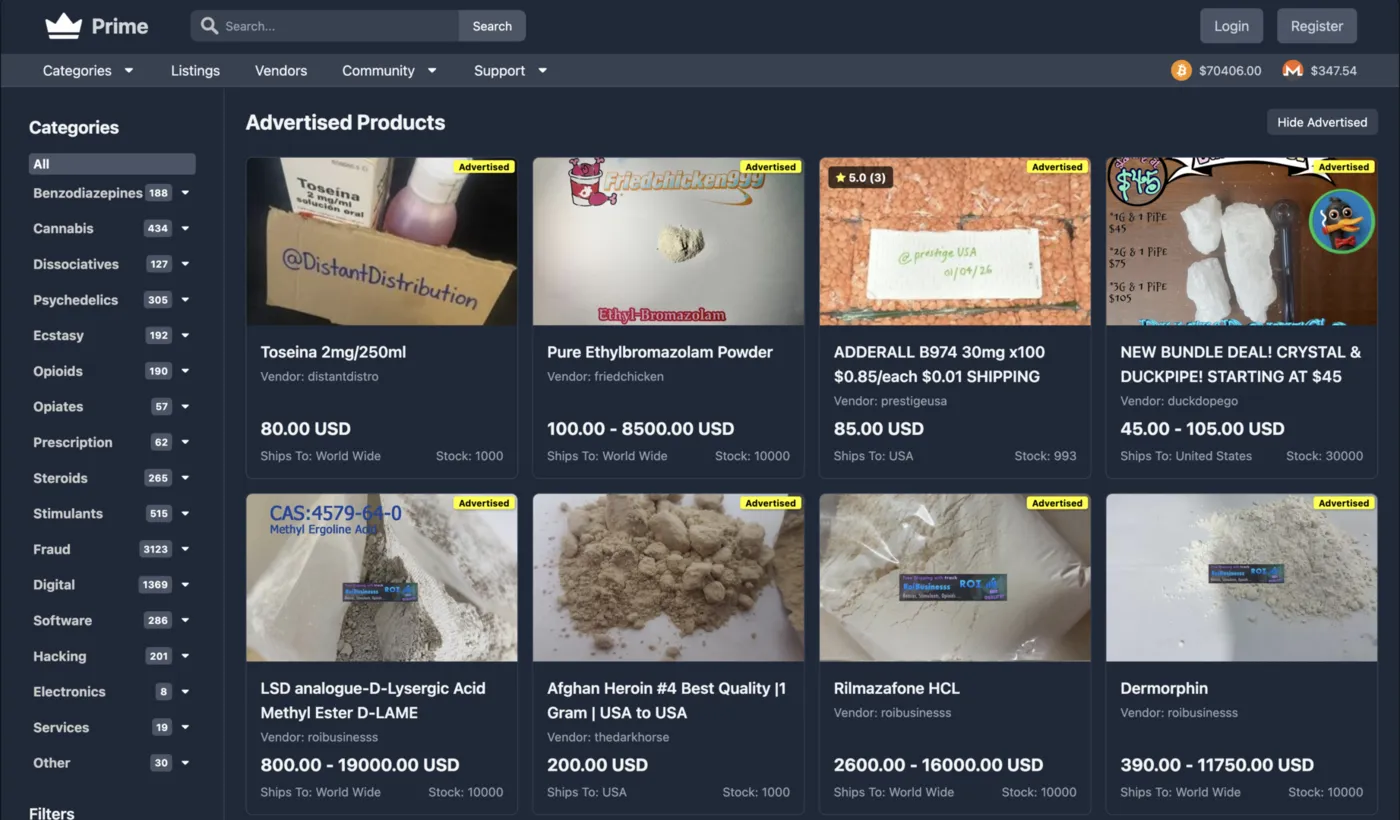
Prime Market Overview
Real-time platform metrics, verified access links, and a comprehensive summary of the marketplace infrastructure powering anonymous commerce.
Detailed breakdown on the status dashboard.
Copy this address into Tor Browser. Compare every character against a trusted source before entering credentials — phishing clones replicate the login page pixel-for-pixel and the URL is your only reliable differentiator.
http://primeyr5lrerg5wigkzd7qp46kaq7f2qco7tgbmdmo2bdvmiwnbixkid.onion
Custom-Built Anonymous Commerce Infrastructure
Most competing marketplaces run on forked source code from defunct platforms like AlphaBay or Hansa. These inherited codebases carry publicly documented vulnerabilities that attackers actively exploit. Prime Market took a fundamentally different approach — building every component from scratch with a custom codebase that has no inherited attack vectors and no known backdoors from previous operators.
The modular architecture allows rapid patching without affecting core functionality. The custom backend handles thousands of concurrent connections while maintaining sub-three-second page loads across all five onion mirrors. Every transaction is governed by a 2-of-3 multi-signature escrow mechanism where neither buyer, vendor, nor marketplace can move funds unilaterally. Both Bitcoin and Monero multisig are fully supported, with transparent dispute resolution staffed around the clock by a dedicated moderation team.
The platform deliberately avoids JavaScript dependencies, eliminating an entire class of browser-based fingerprinting and de-anonymization attacks. Pages render quickly and remain fully functional in Tor Browser's safest security setting. The vendor trust system uses a rolling 90-day weighted algorithm that rewards consistently active, reliable sellers with higher visibility while preventing dormant accounts from coasting on outdated ratings.
Install Tor Browser
Download from torproject.org. Set security to "Safest".
Access the Market
Paste the verified .onion address. Create an account with unique credentials.
Fund & Transact
Deposit XMR or BTC. Browse listings. Multi-sig escrow protects every order.
Multi-signature escrow protects every purchase. Three private keys are generated per transaction — one held by the buyer, one by the vendor, and one by the platform. No single party can authorize fund movement without cooperation from at least one other key holder. This eliminates unilateral seizure risk and ensures that funds cannot be diverted even if the marketplace infrastructure is compromised. The escrow auto-finalization window extends to fourteen days, giving buyers sufficient time to verify delivery before payment is released.
Learn more →Ring signatures, stealth addresses, and RingCT make every Monero transaction private by default. No opt-in toggle required. Bitcoin remains available for users who prefer it, but Monero is the recommended payment method for maximum transaction anonymity on Prime Market. Each deposit generates a unique subaddress, ensuring that multiple transactions can never be correlated on-chain even if they land in the same block. The wallet backend handles all key derivation locally.
Payment details →Vendor trust scores are weighted by recency — the last 90 days matter most. This prevents dormant accounts from coasting on outdated ratings and rewards consistently active, reliable sellers with higher visibility and priority placement in search results. New vendors enter a probationary tier with transaction limits, graduating to higher tiers as they accumulate verified successful transactions and positive buyer feedback over time.
Vendor system →Prime Market deliberately avoids JavaScript dependencies across the entire platform. This is not a design limitation — it is a deliberate security decision that eliminates an entire class of browser-based fingerprinting and de-anonymization attacks. Browser exploits that have successfully identified Tor users in documented law enforcement operations relied almost exclusively on JavaScript execution. By removing JavaScript from the equation entirely, Prime Market ensures that these attack vectors simply do not apply.
Every page on the platform renders correctly and remains fully functional in Tor Browser's strictest security setting. There is zero loss of functionality when you enable the "Safest" mode. If any marketplace requires JavaScript to display content or process logins, that platform is either poorly engineered or actively attempting to fingerprint its users through browser-side code execution.
Five independently operated onion mirrors with automatic load balancing ensure the platform stays accessible even during sustained denial-of-service campaigns. Each mirror runs on geographically separated infrastructure with distinct hosting providers, eliminating single points of failure. If one mirror goes offline — whether from hardware failure, network disruption, or targeted attack — traffic seamlessly routes to the next available instance without any user intervention.
All mirrors maintain a synchronized copy of the platform database through encrypted replication channels with sub-second lag. Account data, order history, and wallet balances remain consistent regardless of which mirror a user connects through. Real-time availability data is published on the status dashboard.
A functional interface that prioritizes speed and security over flashy design. No external CDN calls, no tracking pixels, no unnecessary complexity.
navigate check.torproject.org
> Congratulations. This browser is configured to use Tor.
# Step 2: Access Prime Market
navigate http://primeyr5lrerg5wigkzd7qp46kaq7f2qco7tgbmdmo2bdvmiwnbixkid.onion
> Circuit established: 6 hops (3 client + 3 service)
> Connection secured via .onion v3 protocol
# Step 3: Verify URL character by character
> Match confirmed against trusted source
Prime Market operates exclusively on the Tor network. You will need the official Tor Browser — downloaded from torproject.org — to access any .onion address.
Set your browser security level to "Safest" before connecting. This disables JavaScript entirely, which eliminates browser fingerprinting, prevents exploit delivery through malicious scripts, and ensures your session cannot be correlated with other browsing activity.
For additional protection, consider running Tor Browser from a dedicated operating system like Tails, which routes all traffic through Tor by default and leaves no traces on the host machine after shutdown. See our security reference for detailed recommendations.